Part 1
In this blog post series, we will show you certain steps among with the tools used in order to conduct IoT security assessments. In this first part you will need a .bin file of a device firmware in order to continue.
Tools needed
file
It determines the type of a file. file makes a guess at the type of each file argument by inspecting the attributes and (for an ordinary file) reading an initial part of the file. file compares each file on the command line to templates found in a system-maintained magic file to determine their file type.
https://linux.die.net/man/1/file
xdd
This tool makes a hexdump or do the reverse. xxd creates a hex dump of a given file or standard input. It can also convert a hex dump back to its original binary form.
https://linux.die.net/man/1/xxd
binwalk
A Firmware Analysis Tool. Binwalk is a simple Linux tool for analyzing binary files for embedded files and executable code. It is mostly used to extract the content of firmware images.
https://github.com/ReFirmLabs/binwalk
strings
It prints the strings of printable characters in files. Strings, for each file given, prints the printable character sequences that are at least 4 characters long (or the number given with the options below) and are followed by an unprintable character. By default, it only prints the strings from the initialized and loaded sections of object files; for other types of files, it prints the strings from the whole file.
https://linux.die.net/man/1/strings
Radare2
It is a complete framework for reverse-engineering and analysing binaries; composed of a set of small utilities that can be used together or independently from the command line. Built around a disassembler for computer software which generates assembly language source code from machine-executable code, it supports a variety of executable formats for different processors and operating systems.
hexdump
It displays the contents of a file in hexadecimal, decimal, octal, or ascii. hexdump utility is a filter which displays the specified files, or standard input if no files are specified, in a user-specified format.
http://man7.org/linux/man-pages/man1/hexdump.1.html
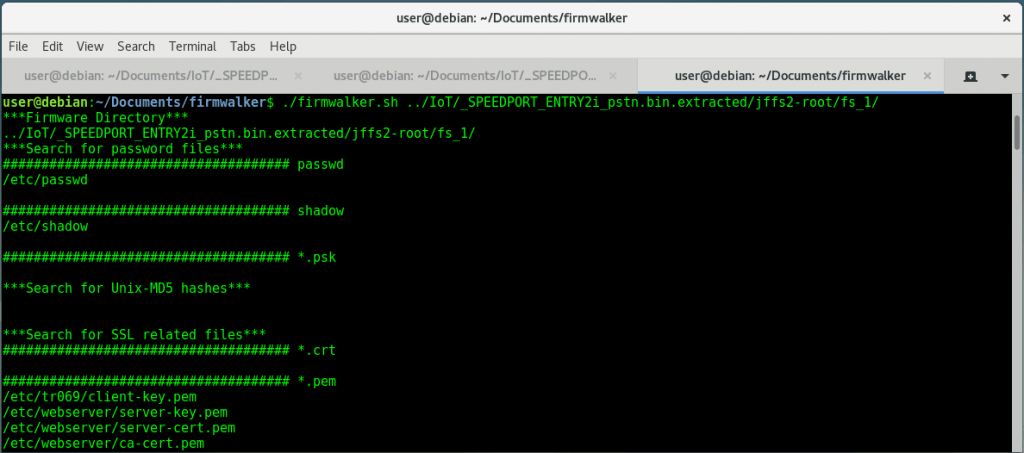
firmwalker
It is a simple bash script for searching the extracted or mounted firmware file system for things of interest such as: etc/shadow, etc/passwd, etc/ssl directory, SSL related files such as .pem, .crt, configuration files, script files, other .bin files, keywords such as admin, password, remote, etc., common web servers used on IoT devices, common binaries such as ssh, tftp, dropbear, etc., URLs, email addresses and IP addresses.
https://github.com/craigz28/firmwalker
Static Analysis
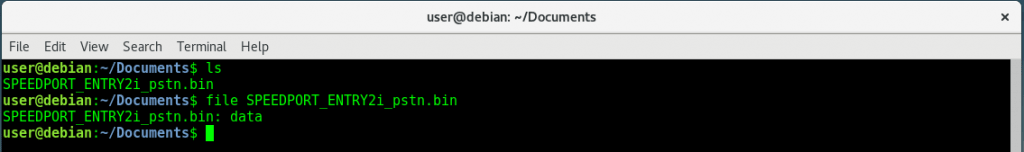
Determining the File Type
file myfile.bin
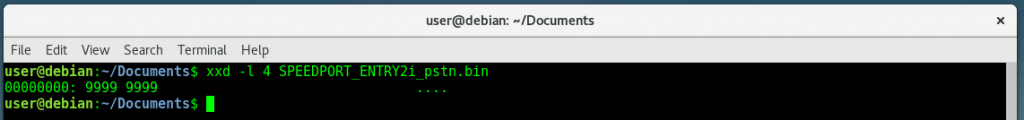
Retrieving file’s Magic Bytes using xxd tool
|
Parameter |
Description |
|
-l <length> |
stop after <length> octets. |
xxd -l 4 myfile.bin
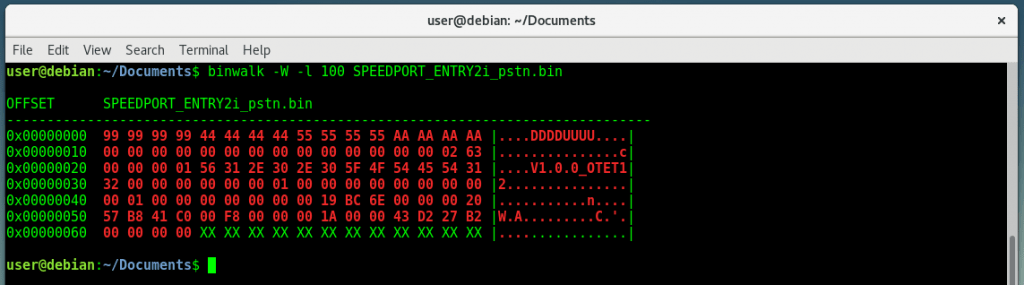
Retrieving file’s Magic Bytes using binwalk tool
|
Parameter |
Description |
|
-W |
Perform a hexdump / diff of a file or files. |
|
-l <length> |
Number of bytes to scan. |
binwalk -W -l 100 myfile.bin
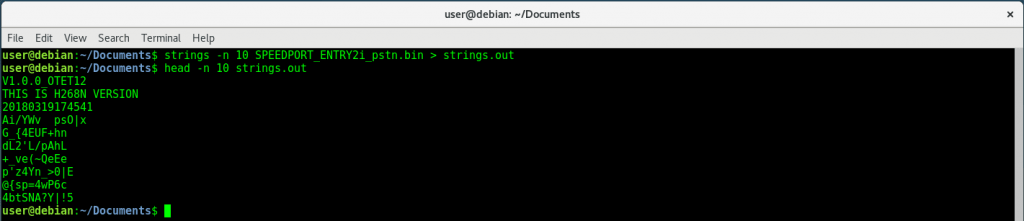
Dumping file’s Strings
|
Parameter |
Description |
|
-n <number> |
Locate & print any NUL-terminated sequence of at -<number> least [number] characters (default 4). |
strings -n 10 myfile.bin > strings.out
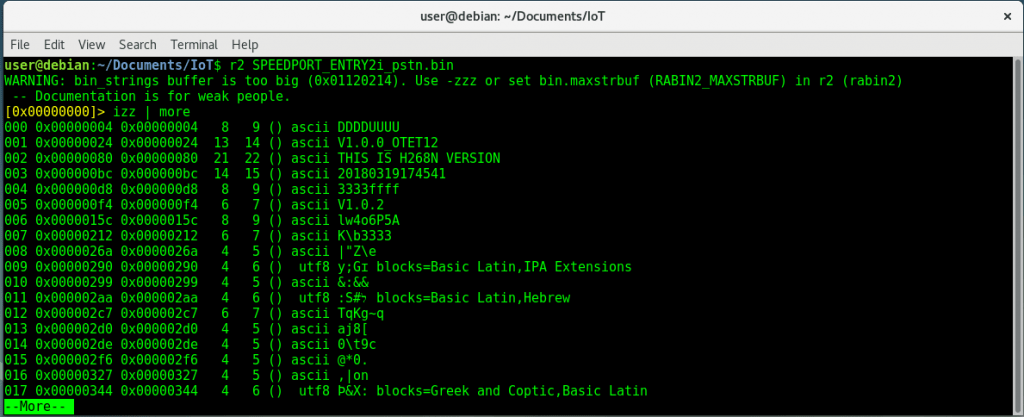
Searching for non-ASCII characters
|
Parameter |
Description |
|
izz |
Search for Strings in the whole binary. |
r2 myfile.bin
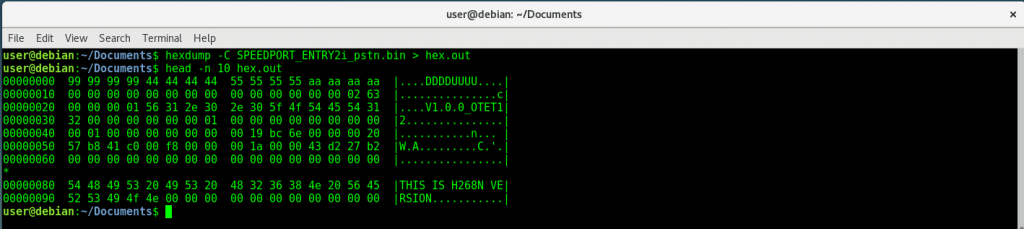
Display file’s contents in hexadecimal
|
Parameter |
Description |
|
-C |
Canonical hex+ASCII display. Display the input offset in hexadecimal, followed by sixteen space-separated, two column, hexadecimal bytes, followed by the same sixteen bytes in %_p format enclosed in “|” characters. |
hexdump -C myfile.bin > hex.out
Analyzing Firmware architecture and its Filesystem
binwalk myfile.bin
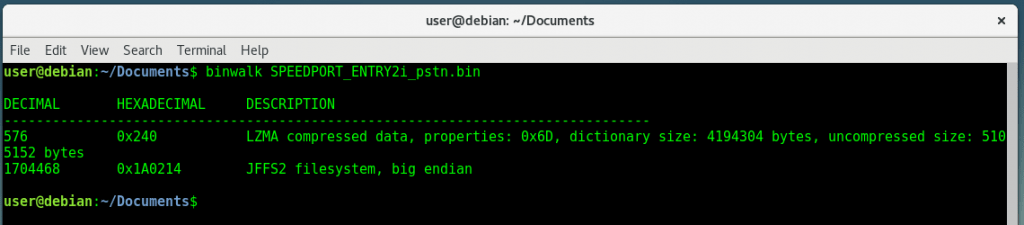
Extracting firmware files automatically
|
Parameter |
Description |
|
-M |
Recursively scan extracted files |
|
-r |
Delete carved files after extraction |
|
-e |
Automatically extract known file types |
binwalk -Mre myfile.bin
or binwalk -Me myfile.bin
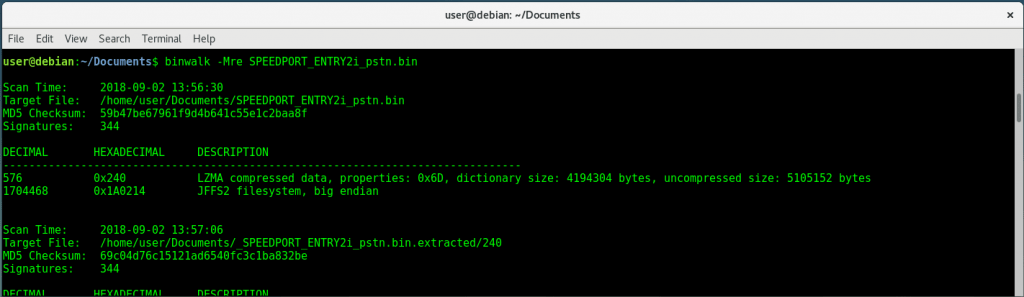
Search the extracted firmware file system for goodies
./firmwalker.sh /path/to/extracted-firmware/root/fs/